Did you know that you can navigate the posts by swiping left and right?
Best fail so far
28 Jan 2010
. category:
Hacking
.
#hacking
#vulnerability
Inteno X5671 VDSL2 box
Basic info
As I’m still moving to a new apartment I have to buy a new VDSL2 box from my operator (DNA). They sell these Inteno boxes by default. First impression was positive, because they use WPA in WLAN by default and password to WLAN is different with each box. Next thing I noticed that there was also SSH available (even tough there is no mention about it in manual), which is extremely great thing!
Software Version: X5671_2.00DNT06
OS: OpenWRT-related system Services:
$ nmap -A 10.0.50.9
Starting Nmap 5.00 ( http://nmap.org ) at 2010-01-28 22:03 EET
Interesting ports on sw9.homelan.lan (10.0.50.9):
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp US Robotics ADSL router firmware update ftpd
22/tcp open ssh?
23/tcp open tcpwrapped
80/tcp open http Comtrend ADSL http config (micro_httpd)
|_ html-title: 401 Unauthorized
| http-auth: HTTP Service requires authentication
|_ Auth type: Basic, realm = DSL Router
Service Info: Device: broadband router
Command line
By default there is telnet and ssh services enabled and you can log in with same users as in web-management. It seems that you can do all the configurations also from command line. More infos: full-command-list.txt command-helps.txt
Funny thing with command line is that they have made some small frontend which is basically almost same thing as sh. And btw. you can access to linux shell (sh) by just typing sh.
Another thing is that there is also user ‘user’, which should have less permission (at least in WEB-management). You can use that user also in command line and there you have all rights to do what you want.
WEB-management
If you have access to WEB-management, you have many ways to exploit box. First problem that I noticed was that since every page seems to be html, there was also cgi-version of that same page. Funny thing is that authentication is only needed to .html-pages. You can just change .html to .cgi and then you can do what you want without any authentication. But that’s not even the best part. :)
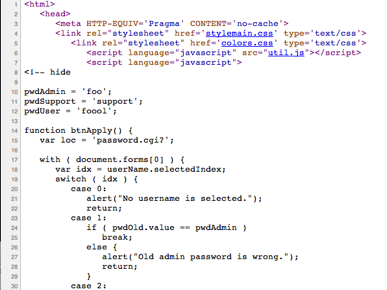
I think the best part is that when you go to http://192.168.1.1/password.cgi and check out the source code you will be surprised. I started tcpdump and watched what’s really happening while doing configuration changes through WEB-management. I noticed that when I try to change password with wrong old password WEB-management informs “wrong password”, but tcpdump shows that there is no packet traffic at that time. I immediately figured out that browser has to know old password already and it is possible to find out. I totally dropped when I found this from the source code of that password.cgi -page:
<html>
<head>
<meta HTTP-EQUIV='Pragma' CONTENT='no-cache'>
<link rel="stylesheet" href='stylemain.css' type='text/css'>
<link rel="stylesheet" href='colors.css' type='text/css'>
<script language="javascript" src="util.js"></script>
<script language="javascript">
<!-- hide
pwdAdmin = 'admin';
pwdSupport = 'support';
pwdUser = 'user';
...
Same in short: You can go to the password change page without authentication and check out the page source code and you have admin, support and user password as in plain text. (in example code you can see default passwords).
Same in short: You can go to the password change page without authentication and check out the page source code and you have admin, support and user password as in plain text. (in example code you can see default passwords).
Afterwords
Since outsiders should not have access to management by default these security problems are not so catastrophic. Still this is quite a funny example how awful (funny) the situation with these kind of home boxes sometimes is.
ps. it seems that I don’t have any use for this box even though my operator said that I have to buy this box. My new apartment has new cabling and there is just boxes with RJ45 connectors.
Edit 2010-03-05
I reported this problem immediately to CERT-FI and they contacted to Intento and at the moment there is new firmware available. New firmware is distributed by operator so I still have to wait to get hands dirty with the new firmware, where the problems should be fixed. Thanks to very helpful people in CERT-FI. :)
Edit 2010-04-12
Firmwire update is finally available (to DNA users) in DNA Web-pages.
