How my application ran away and called home from Redmond
I recently found a surprising leak vector in Windows 10 installations. We were porting our Beacon Application to Windows and for easy deployment. The plan was to create just one .exe including everything. However we found out that End Point Protection (EPP) solutions didn’t like that at all and we had to go with the MSI installer option. This is a story what happened during the .exe testing.
I used my personal malware analysis lab for testing the application. My lab is an isolated network environment which has a whitelist based firewall rules. Whitelist firewall is needed to carefully allow specific updates and downloads. The lab already has Beacon Virtual Machine running and it has found issues in the past. All of them are fixed. So this leak was something new!
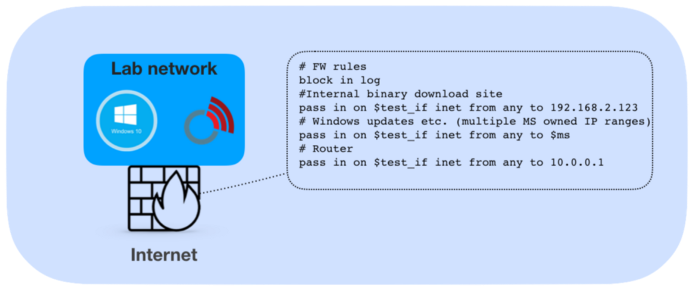 …
…